Akord's encryption and cryptographic primitives
End-to-end encryption ensures that the only ones who have the ability to decrypt the data are the sender and receiver.
 3 min
3 minWhy end-to-end encryption?
Many service providers offer encryption in transit (HTTPS connection) and encryption at rest (data is stored encrypted on the servers). However, this does not prevent third parties from accessing sensitive user data. For example, company employees, selling data for advertising purposes or a server attacked by hackers.
End-to-end encryption ensures that the only ones who have the ability to decrypt the data are the sender and receiver. No encryption backdoor is possible.
There are two types of end-to-end encryption: symmetric and asymmetric.
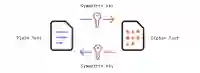
Symmetric encryption
The data is encrypted and decrypted with the same unique symmetric key. So the encryption requires the knowledge of the key by the sender and the receiver. The challenge is to exchange this key securely while preventing it from falling into the hands of a third party.
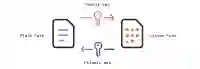
Asymmetric encryption
With asymmetric encryption each participant has their own public & private key pair to communicate. The public key can be openly distributed, while the private key should be kept secret. The data is encrypted with the recipient’s public key, so that it can only be decrypted with their private key.
Although asymmetric encryption is considerably less efficient than symmetric encryption, its main advantage is that it does not require prior key agreement and thus the key exchange can be safely carried out through the network.
Akord’s encryption
In addition to encryption in transit and encryption at rest, all exchanged data on Akord is end-to-end encrypted. In other words, everything is encrypted locally, before it ever leaves your device.
We use industry standard algorithms to perform all cryptographic operations.
For performance, we use hybrid encryption, meaning that data is encrypted using a unique symmetric key, and then that key is encrypted with the recipient's public key using asymmetric encryption.
It also means that encrypted data can be stored in the cloud once, and access to it can be managed at the key re-encryption level.
Both the symmetric and asymmetric encryption we use apply authentication under the hood, so that data integrity is always ensured and cannot be tampered with.
Cryptographic primitives
Cryptographic primitives are well-established algorithms that are commonly used to build cryptographic protocols for security systems.
- library: WebCrypto API
- algorithm: SHA-256
Key derivation function
To obtain a strong encryption key from a user password, we use the Password-Based Key Derivation Function 2 (PBKDF2) by adding a random salt to the password and performing 150000 iterations of the SHA-256 hash function.
- library: WebCrypto API
- algorithm: PBKDF2 with HMAC-SHA-256
Symmetric encryption
Any data exchanged within the Akord system is encrypted using a unique, randomly generated symmetric key via AES256-GCM with a random initialisation vector (IV) prepended to the encrypted data.
- library: WebCrypto API
- algorithm: AES256-GCM
Asymmetric encryption
We use asymmetric encryption for data access control, the symmetric keys used to encrypt the actual data are then encrypted with the recipient's public key by performing a Diffie–Hellman (DH) key exchange on a Curve25519 elliptic curve.
An ephemeral key pair is generated to establish a key agreement. Once the symmetric key is agreed upon, the data is encrypted using XSalsa20 stream cipher. A random, unique nonce is also generated and used for Poly1305 MAC authentication.
- library: libsodium
Algorithms:
- key exchange: X25519
- encryption: XSalsa20 stream cipher
- authentication: Poly1305 MAC
Digital signatures
All data is signed using the Edwards-Curve Digital Signature Algorithm(EdDSA) with the SHA-512 hash function and Curve25519 elliptic curve.
- library: libsodium
- algorithm: Ed25519
Learn more
Interested in more on this topic? Check out these related articles:
Make your first upload to Arweave for free
Upload public or private data to Akord’s digital vaults. The only app to provide free storage on the Arweave blockchain.



