Own the keys, own your data
We'll explain the backup phrase, how we store and manage it on Arweave, and demonstrate exactly how you 'own the keys.
 4 min
4 minWith Akord, you own the keys that encrypt and decrypt your data. Your keys are generated when you sign up and are represented by your backup phrase. In this article article, we'll explain the backup phrase, how we store and manage it, and demonstrate exactly how you 'own the keys'.
Your backup phrase explained
For many web3 services, the backup phrase is required any time you would like to access your wallet from a new device. Let's first explain what the backup phrase is.
In order to generate unique keys, we need a unique random number that is known as a “seed”. Since it is difficult for us to read a large number, crypto-wallets use a backup phrase, which is a human-readable representation of the seed. It is also known by other names such as seed phrase, recovery phrase, mnemonic, or passphrase.
The backup phrase is typically generated using an algorithm called BIP39 and assigned to a user when signing up. Akord uses this method to generate the backup phrase. It consists of 12 or 24 words that are chosen from a list of 2,048 words beginning with “abandon” and ending with “zoo”.
How safe is a backup phrase that is made up of 12 words? Well, since there are plenty of possible combinations, the chance of drawing the right combination is 1 out of the big number below:
2,048^12 = 5444517870735015415413993718908291383296 ≈ 5.4445179e+39
So, as you can see, backup phrase is pretty much impossible to hack from a brute force attack that tries to guess what your backup phrase is. You just need to store it in a safe place.
We recommend the following security practices:
- Store your backup phrase in a few different secure locations offline.
- Don’t communicate your backup phrase to anyone.
- Don’t store your backup phrase unencrypted digitally.
You own the backup phrase on Akord
In Akord, we ask for an email address and password. We ask for your email so we can send you important notifications when other people in your vault take actions. Your password is used to decrypt your backup phrase locally when you want to sign in.
The backup phrase is encrypted using your actual password. This means that nobody can decrypt your backup phrase without knowing your password.
We store the following three things in our database:
- E-mail address
- Encrypted backup phrase
- Verifier of the password
We do not store your password, but rather a cryptographic verifier of it. This means that we can easily check if a password you entered is correct without ever seeing the password itself. For those who are curious about how this works in detail, you can read about this process in the Secure Remote Password protocol (SRP).
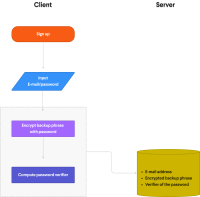
So here’s the process when you sign up with your email address and password. First, we encrypt your backup phrase with the password you entered, or more precisely, with a key derived from your password using PBKDF2. Then, we use the SRP protocol, to compute a cryptographic verifier: We send these two pieces of information along with your email address to our server. This makes it impossible for any middleman, or for anyone with access to the data, including Akord, to decrypt your backup phrase or obtain any information about your password.
Akord’s simple sign in
Most web3 services require you to connect with a wallet, but with Akord you just need your email and password. So how exactly are you using your keys to sign in?
When you sign in, we first look up your email address and use the SRP protocol to make sure that the password you provided is correct, again, without actually sending the password. If the provided email and password are correct, we send back the encrypted backup phrase. It is decrypted directly in your browser, meaning that nobody but you ever knows it.
At this point, you're ready to use our user-friendly UI to upload your files to Arweave, with all encryption and decryption happening directly in your browser .
––
We believe in true collaboration with the people using our product. If you have feedback on Akord, the best place to reach us is by becoming part of our community on Discord.
Chat with our community
Talk to other members of our community, ask questions and get the heads up on all the latest Akord happenings.



